ProcessDolphin
Specialized network monitoring tool for per-process traffic analysis in real-time
Precisely correlates network activity with individual processes, providing detailed visibility into which applications are communicating across your network and where
Network Process Mapping
Track, visualize, and analyze per-process network traffic with detailed precision
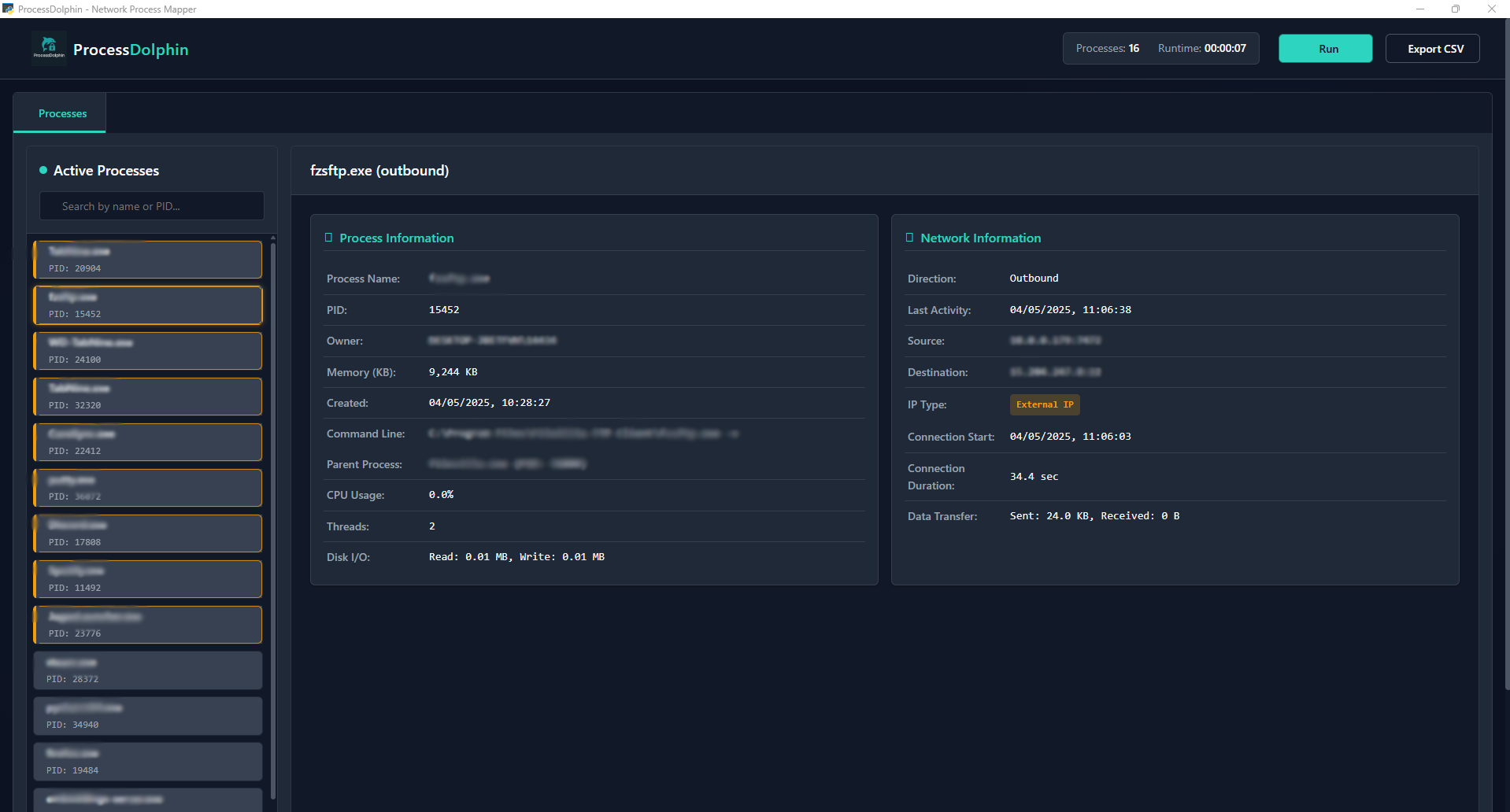
ProcessDolphin links network activity to specific processes, providing comprehensive visibility into connection endpoints, data transfer volumes, and communication patterns for each application on your system.
Real-Time Traffic Monitoring
Monitor which processes are establishing network connections with comprehensive connection metadata and direction tracking.
Low System Footprint
Engineered for efficiency with minimal CPU usage while monitoring all active network connections and processes.
Process Connection Mapping
Immediately identify which processes are communicating with external systems through detailed protocol analysis and connection tracking.
Export Capabilities
Generate detailed reports in multiple formats including CSV and PCAP for further analysis and integration with other security tools.
Comprehensive Process Monitoring
Real-time insights into process behavior and network activity
Complete Visibility Into Process Network Activity
ProcessDolphin provides comprehensive information about each process with network connections:
- Process Context: Executable name, PID, user/owner, memory usage, and creation time
- Connection Details: Complete connection tuples, direction, duration, and data transfer metrics
- Performance Metrics: Real-time CPU usage, thread count, and disk I/O operations
- Process Hierarchy: Parent-child relationships and process lineage
- Execution Environment: Full command line arguments and process creation context
system_process.exe
PID: 12345See ProcessDolphin in Action
Intuitive interface for monitoring process network connections
ProcessDolphin provides a clean, intuitive interface for monitoring network connections by process. Quickly identify applications communicating with external networks, analyze connection patterns, and export comprehensive reports for further analysis.
Real-World Applications
How cybersecurity professionals and IT teams use ProcessDolphin
Monitor Network Connections
Keep track of which processes are connecting to the network:
- View all network connections from running processes
- Monitor data transfer volumes for all connections
- Track which processes are reaching out to external servers
- Analyze process-to-network relationship patterns
$ dolphin --monitor-outbound --detailed
[*] Monitoring outbound connections...
[*] Connection detected:
Process: background_service.exe (PID: 3342)
Destination: 185.128.43.71:8080
Data sent: 236.4 KB
Connection duration: 00:05:37
[*] Export command: dolphin --export-process 3342 --format json
[*] Connection details logged to /var/log/dolphin/connections.jsonDetailed Network Forensics
Perform comprehensive analysis of network traffic by process:
- Track data flow between processes and remote endpoints
- Generate connection timelines for incident response
- Export detailed logs for compliance documentation
- Map internal network communications patterns
$ dolphin --generate-timeline --process firefox.exe
[*] Generating connection timeline for firefox.exe
[*] Found 47 connections in the last 24 hours
[*] Top domains by traffic volume:
1. cdn.example.com (45.2 MB)
2. api.service.com (12.8 MB)
3. analytics.site.net (5.3 MB)
[*] Timeline exported to /forensics/firefox_connections.json
[*] Connection map visualization saved to /forensics/firefox_map.htmlPerfect for Cybersecurity Education
An ideal tool for students and educators:
- Visualize how applications communicate on networks
- Learn to understand process-to-network traffic patterns
- Practice network forensics techniques
$ dolphin --education-mode --scenario network_monitoring
[*] Loading educational environment...
[*] Scenario: Network Connection Analysis
[*] Start the analysis by examining the following:
1. Which processes are establishing network connections?
2. What data volumes are being transmitted?
3. Map the relationship between processes and destinations
[*] Use 'dolphin --hint' if you need assistance
[*] Complete the exercise by documenting all active
connections and their associated processesVisualize Your Network Activity
See exactly which processes are connecting to the internet and how they're communicating.
Built for Network Visibility
Designed for IT professionals, security teams, and technology students
Cybersecurity Engineers
Map process-to-network relationships with granular detail for threat hunting and incident response. Identify suspicious connections and data exfiltration attempts in real-time.
- Process network behavior analysis
- Granular connection metadata
- Suspicious connection alerts
- Forensic data export capabilities
IT Departments
Monitor network usage by process to troubleshoot connectivity issues, optimize bandwidth, and ensure proper application behavior across your organization.
- Application connectivity monitoring
- Data transfer volume analysis
- Process resource utilization
- Network traffic optimization
Computer Science Students
Visualize and understand process-to-network relationships for hands-on learning in cybersecurity, networking, and system administration courses.
- Network security fundamentals
- Process behavior visualization
- Practical security monitoring
- Digital forensics learning
Join Our Community
Connect with fellow security professionals and the ProcessDolphin development team